Phishing metrics - what to track?
The results of phishing campaigns are often not comparable with each other over time. Various security vendors and red teams use different tooling and techniques - which is totally fine.
However, I recommend requiring tracking a minimum set of metrics to be able to compare results over time.
Funny side facts: At times employees are messing with the red team, entering invalid creds for CISO or CEO and things along those lines. Some employees (often engineers) are curious and open the link in isolated VMs to debug and explore the phishing site.
These side effects make phishing stats that don’t track various stages precisley less meaningful.
A phishing campaign should track the following data points at a minimum to provide insights:
- Were security controls artificially weakened? Yes/No - some vendors might require to be whitelisted, a red team (hopefully) tries to circumvent controls.
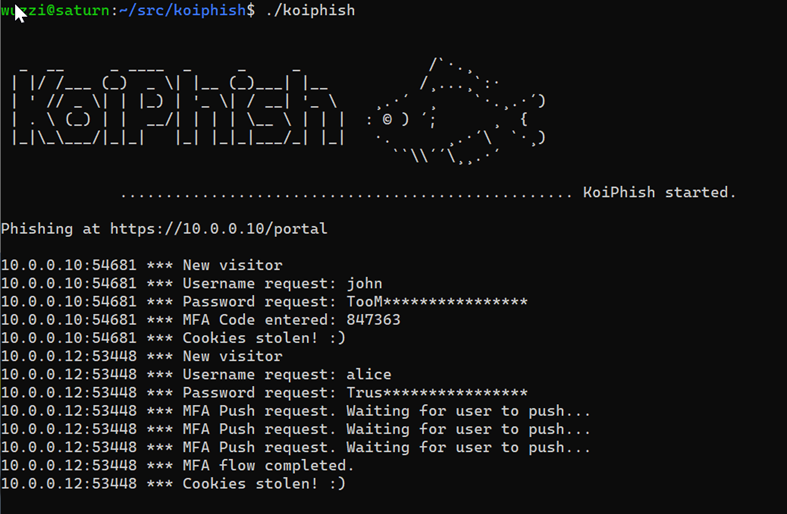
- Number of users the phishing email was sent to
- The bounce rate - were any of the mails outright rejected?
- Number of users who opened/viewed the email - rough approximation via a tracking pixel in email
- Number of users who clicked the link
- Number of users who entered valid username - must match some identifier in email to filter out, and identify, trolling.
- Number of users who entered a password
- Number of users who entered their valid(!) password
- Number of users who entered MFA/code or submitted a push notification - more variants possible, can be split out by MFA method (push, text message, authenticator app code,…)
- Number of users who’s auth cookies got stolen (full compromise)
- Number of users who reported the phish
Its best to also provide the ratio for each of the metrics. Without sharing the details its at times difficult to compare phishing results. If you do excercises in purple teaming fashion you can get more precise information around delivery and who viewed/reported/deleted it and also measure if blue team is able to block ongoing attacks => Get a metric from first report to active block/mitigation being put in place (mean-time-to-block) MTTB.
Interesting fact: What I have seen is that the number of users entering their valid password and those that complete the MFA flow on the phishing site is often nearly the same - more then 90% of users who entered their password, will also complete the MFA login flow on the phishing site.
Clients are at times still surprised that a full account compromise is possible, even though MFA is in place. Deployment and adoption of security keys (usage of WebAuthN and FIDO2) is less well understood. We need to continue advocating for broader adoption.
If you found this interesting and informational, feel free to follow or DM me on Twitter: @wunderwuzzi23
For phishing campaigns WUNDERWUZZI uses a variant of KoiPhish.